I have a short email address. Those that know, know, so not posting here.
Suffice to say it is of the form x@x.xx so is only 6 characters. It is 100% valid. I have used it for a couple of decades now - this is not new. I am not alone. [side note, I tried to sort x@xx email, which is not easy, and did not get off the ground, but some people have done this, and it is valid]
I registered to get access to on-line COVID passes with the NHS or is it NHS Digital, or what? To be honest it is not 100% clear. Privacy policies and the like should make this clear, but even now I am not sure. My MP believes it is Welsh government. The fact I am not 100% sure is part of the problem.
[update: https://access.login.nhs.uk/privacy says it is joint data controllers of the devolved (Welsh) administration and NHS Digital]
They would not allow me to register, so I created a temporary address (longer) and registered. Simple. I even have the whole domain rfc2822.uk for this purpose.
I then tried to change the email address to my normal x@x.xx email address, and their system would not accept it.
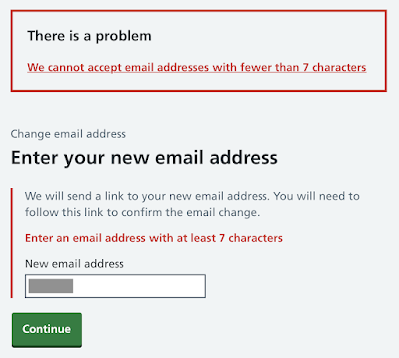 |
| NHS expecting me to change my personal data to fit them |
So I emailed their data controller requiring them, under my right of rectification under (UK) GDPR to correct my email address. They refused. Note the original (temporary) email is no longer valid, and hence meets the definition of not "accurate" personal information. Indeed, I do not even have the domain any more.
I wrote to ICO, and have exchanged several emails to ICO, and escalated and asked for review of the case.
Basically the ICO said: There is nothing in data protection legislation that prevents an organisation from having a system that has a minimum requirement for an email address.
This seems odd, as how can an organisation accurately record personal information if they do not accept a valid email address, i.e. they have a "minimum requirement" for what is "valid"?
This has gone on for some time, and I am not alone, there are others I know with similarly short email addresses that have issues with NHS (and other organisations). There are others I know with related issues on incorrect data validation at "sign up".
Just to be 100% clear, the NHS fully accept my email address is a valid email address, and have emailed me, to that email address, to say so, as have ICO.
I also asked ICO more generic questions about whether an email address is personal information, and if I can expect (require) an organisation to correct it when it is wrong. They confirmed that is the case, so I again wrote to NHS quoting them - no reply. What a surprise.
I have written to my MP as well, and asked them to chase, and they have written to NHS (Welsh Government).
Latest from ICO is "
For clarification, as the NHS has not recorded your email address then we are unable to suggest that they are recording inaccurate information. 'Inaccurate' would apply to information that was recorded incorrectly. There is no suggestion that they have done this."Seriously, I'm shocked. This has, all along, been about the NHS refusing to correct my email address. So I have explained, again, to the ICO, that the NHS have recorded my wrong email address and are refusing to enact my request under my right to rectification to correct it under UK GDPR.
We will see how it goes, but this is a matter that relates not just to email, but other things.
- Organisations will insist someone has to meet some format for a name - a forename and surname (not all have this), a name with more than one letter (not all have this), etc.
- Organisations will insist a UK mobile phone number has to start 07, and organisations will even blacklist some operators 07 mobile numbers as not valid mobile numbers!
- Organisations routinely try to impose rules on email addresses.
- I really expect organisations to have shit when it comes to recording gender, which is rather topical.
The law does not stop companies from having rules to take their service as long as not discriminating based on some protected criteria. They can refuse me because my email address is too short. IMHO this is wrong.
But once they have accepted a customer/client, perhaps with wrong, or temporary personal details, they do have to comply with GDPR and have to correct incorrect personal information. So it would be better if they accept the correct personal information in the first place. In seems to me that GDPR (or UK GDPR) has a flaw in not covering this properly for "sign up". People should not be able to use email address, mobile number, name, or gender, as a reason to refuse to accept a customer/client.
This is even more so when it is not some company, but an organisation like the NHS. I have an NHS presence, I have to, as a UK citizen, and they have data on me right now that is not "accurate". That needs fixing.
Update: 1st Jul: The ICO now seem to be suggesting that because the email address they recorded at the time was correct (accurate) that they do not have to correct it now that it has become inaccurate. This would suggest organisations do not have to update name, address, phone number, email address, well, any personal information they hold when it becomes inaccurate over time. That seems a stretch!
Update: Someone has suggested this is "the same on all GDS platforms", and that it is not fair for me to "bother" the NHS. I appreciate the NHS have a hard time, but if this is the case the all the NHS have to do is contact whoever maintains their platform for them, explain they have a legal requirement to correctly record personal data, so have 30 days to "fix" this, and the NHS will have done what they need. Instead the NHS have so far chosen to spend time arguing with me, and then updating their site to state that an email address has to be at least 7 characters (previously it accepted it but did not send the confirmation email so it did not work). At the end of the day, someone, somewhere, on some platform, just has to change a 7 to a 6 in some code (or better still, follow the RFC for validating email, which will be a simple regex or library). It is not a hard fix for whoever does it - if the layers of people above that, all the way to the NHS, simply tell them to do it.